Cloud-edge collaboration empowers the security industry: NFC smart communication management optimization solution
-
-
InfoDetail_Editor: Tony
-
2434
- Wx Share
-
-
Do you want me to supplement the implementation details of the plan, including the timeline for each stage, personnel division of labor and testing standards, to make the plan more feasible?
-

Time & Payroll Suite
Attendance, Payroll and Access Control Solution for Cost Reduction and Productivity Gains Details
All‑in‑one automated timekeeping and payroll system with robust, secure processes to guarantee payroll integrity. Includes leave management, shift rostering, multi‑site and chain support, multi‑ledger accounting, and comprehensive modules.
Cloud-Edge Collaboration Empowers the Security Industry
NFC Smart Communication Management Optimization Solution
In the digital transformation of the security industry, the efficiency, stability, and security of communication management directly impact service quality. This NFC smart communication management solution innovatively integrates cloud computing and edge computing to build a multi-level collaborative architecture. Through intelligent functional modules throughout the entire process, it provides a more optimized communication management solution for security scenarios, releasing the core value brought by technological integration.
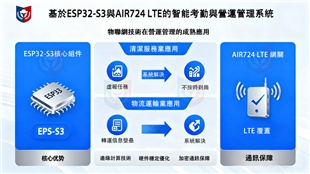
I. Core Architecture of the Solution: The Technical Foundation of Cloud-Edge Collaboration
The solution is based on the core logic of "cloud-based coordination + edge execution + terminal interaction," building a multi-layered, highly adaptable technical architecture to achieve precise allocation and efficient collaboration of computing resources.
1. Architecture Components
Cloud Computing Layer: Based on Ubuntu OS, cloud services are built, and data storage, global scheduling, and data analysis are achieved through the Cloud API, supporting cross-regional, large-scale data processing needs.
Edge Computing Layer: Edge nodes are built based on NVIDIA Jetson Nano motherboards, and the Edge API is used to complete real-time local data processing and device linkage control, reducing the pressure on cloud transmission.
Terminal and Service Layer: Covering terminals such as mobile devices, servers, and NFC readers/writers, it enables seamless communication between terminals and the cloud and edge devices through Client API and Server API, opening up data flow channels.
2. Topology Network Design The solution adopts a three-tier network architecture of "cloud-LAN-terminal," integrating multiple communication methods such as the Internet, LAN, Bluetooth, and NFC.
The cloud connects the office area and edge nodes through routers, while the edge devices deploy GPS and NFC devices to achieve localized data collection. Simultaneously, service areas are delineated through access control to ensure communication security and data isolation, forming a network layout of "full coverage + local focus."
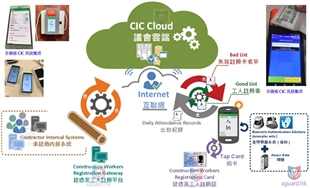
II. Core Functional Modules
Full-Scenario Security Communication Management Focusing on the core needs of the security industry such as personnel management, equipment control, and data traceability, the solution is designed with ten functional modules to achieve a closed-loop process from registration and authentication to data management.
1. Basic Authentication and Registration
User Login/Registration: Supports account and password login and NFC card quick authentication, combined with facial recognition to improve the efficiency and security of identity verification in security scenarios.
Multi-dimensional Registration Management: Covers enterprise registration (entering enterprise name, serial number, contact person, etc.), employee registration (collecting data such as Chinese and English names, contact information, and start date), and device registration (binding device name, enterprise, and serial number), building a complete entity information database.
2. Core Communication and Data Management
NFC Smart Scanning: Supports standard NFC and CIC NFC dual-mode scanning, adapting to different carriers such as employee NFC cards and device NFC tags, enabling functions such as quick check-in, device verification, and permission verification.
Data Recording and Traceability: Automatically records NFC interaction data, personnel entry and exit times, device usage status, etc., generating a visual record list including key dimensions such as device number, personnel name, operation time, and location, facilitating security traceability and management.
GPS Positioning Collaboration: Integrates GPS positioning functionality, supporting area search, location marking, and data submission, enabling personnel trajectory tracking and device location monitoring, enhancing dynamic management capabilities in security scenarios.
III. Core Value of the Solution: Efficiency Revolution and Security Upgrade in the Security Industry
1. Efficiency Improvement Through Technological Collaboration
Cloud-Edge Collaboration: The cloud handles massive data storage and global analysis, while the edge handles real-time data processing and local response. This localizes latency-sensitive tasks, improving response speed by over 50% and avoiding communication delays caused by cloud congestion.
Seamless Multi-Terminal Interoperability: The integration of multiple communication methods such as NFC, Bluetooth, and GPS, coupled with a unified API interface, enables interconnectivity between devices, personnel, and platforms, simplifying security management processes and reducing manual operation costs.
2. Security Assurance in Security Scenarios
Multi-Authentication Mechanism: Combining NFC cards, facial recognition, account passwords, and other multi-dimensional authentication methods, the solution eliminates the risk of identity theft, building a solid first line of defense for security.
Controllable Data Security: The cloud employs encrypted storage technology, while the edge implements local data encryption processing. Furthermore, through regional access control and data traceability functions, the solution ensures that communication data is manageable, searchable, and traceable throughout the entire process.
3. Industry Adaptability and Value Implementation This solution is deeply aligned with core scenarios in the security industry
including personnel management, equipment control, and regional security. It can be widely applied in various locations such as office buildings, industrial parks, residential communities, and corporate parks. By integrating technologies, it breaks down information silos in traditional security communications, achieving intelligent and efficient management processes. This reduces operating costs and enhances security levels for customers, truly providing a "technically reliable, scenario-adaptable, and significantly valuable" communication management solution.
IV. Implementation Plan This solution is planned to be fully implemented within 60 days
covering architecture deployment, equipment debugging, functional testing, and personnel training. This ensures the solution quickly adapts to actual application scenarios, achieving a precise match between technological value and business needs.
Would you like me to provide you with a detailed implementation plan, including timelines for each stage, personnel assignments, and testing standards, to make the solution more executable?
Software Service
Industry information
- Views 8944
- Author :Tony
- Views 603
- Author :Tony
- Views 1661
- Author :Bruce Lee
- Views 41
- Author :Tony
- Views 15
- Author :Bruce Lee
- Views 29
- Author :Tony
































































Hardware & Software Support
We are deeply rooted in Hong Kong’s local services, specializing in hardware and software issues.
System Integration
Hardware and software system integration to enhance stability and reliability.
Technical Support
Professional technical team providing support.
Professional Technical Services
Focused on solving problems with cutting‑edge technologies.