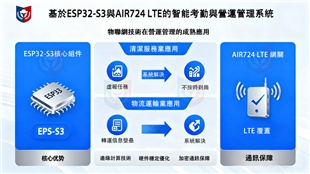
Intelligent attendance system based on ESP32-S3 and Air724 LTE edge computing
-
-
Author: Tony
-
41
- Wx Share
-
-
Edge computing is reshaping modern operational governance and providing solutions for government compliance.
-
Time & Payroll Suite
Attendance, Payroll and Access Control Solution for Cost Reduction and Productivity Gains Details
All‑in‑one automated timekeeping and payroll system with robust, secure processes to guarantee payroll integrity. Includes leave management, shift rostering, multi‑site and chain support, multi‑ledger accounting, and comprehensive modules.
Intelligent Attendance and Compliance Monitoring Solution Based on ESP32-S3 and LTE Edge Computing System
Introduction: Edge Computing Reshapes Modern Operations Monitoring
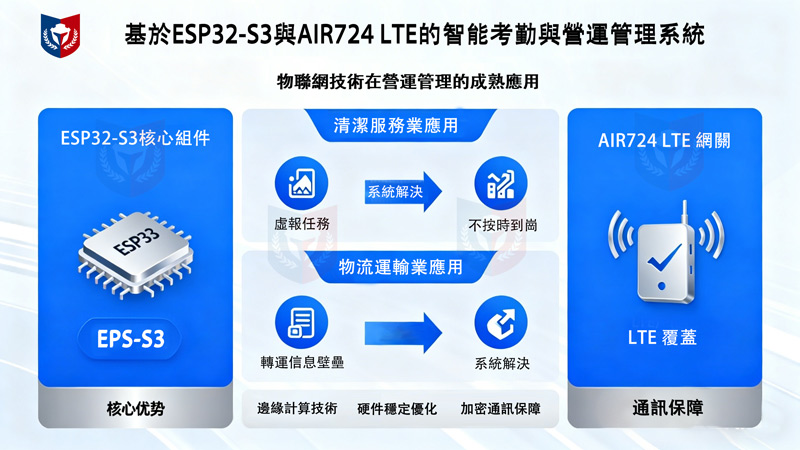
In the development of IoT technology, edge computing has moved from proof-of-concept to large-scale commercial applications. Especially in labor-intensive service industries and logistics transportation, traditional operations monitoring methods are facing unprecedented challenges. Issues such as false reporting of tasks in the cleaning service industry and collusion and fraud in the logistics transportation industry not only cause direct economic losses to enterprises but may also trigger legal disputes and brand reputation crises. This article will detail how to use the ESP32-S3-DEV-KIT-N16R8-M development board in conjunction with the Air724 LTE edge computing gateway to build a stable, efficient, and compliant intelligent attendance and work verification system, addressing the aforementioned industry pain points from a technical perspective.


Chapter 1: ESP32-S3 Technical Architecture and Performance Advantages
1.1 Hardware Architecture Design Philosophy
The ESP32-S3-WROOM-1 module adopts Espressif Systems' most advanced IoT chip architecture, specifically designed for high-reliability edge computing scenarios. Its core features are:
Dual-core processor architecture:
Equipped with an Xtensa® 32-bit LX7 dual-core processor with a clock speed of up to 240 MHz
Core division of labor: One core focuses on sensor data acquisition and real-time processing, while the other core handles communication protocols and network transmission.
Efficient data exchange mechanism between the two cores ensures system response latency of less than 50ms.
Optimized memory configuration:
Built-in 512KB SRAM to meet the memory requirements of complex algorithms.
External 16MB Flash storage space to accommodate various AI models and historical data.
Independent RTC memory for data retention in low-power states.
1.2 RF performance and communication stability
Enhanced RF circuit design:
Four-layer PCB design with a dedicated RF ground plane.
Integrated π-type matching circuit for optimized antenna impedance matching.
Receiver sensitivity reaches -98 dBm (typical value), maintaining stable connectivity even in complex environments
Multiple Communication Interface Support:
Supports 802.11 b/g/n Wi-Fi protocol, 2.4 GHz band
Bluetooth 5.0/5.1 LE protocol, supporting long-range transmission mode
Rich peripheral interfaces: SPI, I2C, I2S, UART, PWM, etc.
1.3 Power Management and System Stability
Advanced Power Management Unit:
Operating voltage range: 3.0V - 3.6V, adaptable to various power supply environments
Multiple power modes: Active mode, modem sleep mode, light sleep mode, deep sleep mode
Ultra-low power coprocessor (ULP): RISC-V core, power consumption only 10µA, can perform simple monitoring tasks when the main core is in sleep mode
Temperature Stability Guaranteed:
Operating temperature range: -40°C to 85°C
Built-in temperature sensor enables dynamic temperature compensation
Thermal Design Power (TDP) control prevents overheating and frequency throttling

Application based on ESP, stable performance, physical security technology
Chapter 2: Edge Computing System Architecture Design
2.1 System Overall Architecture
This system adopts a layered edge computing architecture, including the following four layers:
Terminal Perception Layer:
ESP32-S3 development board as the main controller
NFC M4255 RF chip module, supporting ISO 14443 A/B protocol
2-megapixel camera lens module, supporting face detection and recognition
GPS/BeiDou dual-mode positioning module
Ambient light sensor and motion sensor
Edge Computing Layer:
Local AI inference engine: executes a lightweight face recognition model
Data Preprocessing Module: Filters, validates, and compresses sensor data
Rule Engine: Executes predefined business rules and validation logic
Network Transport Layer:
Air724 LTE CAT4 module, supports all network types
Dual SIM card backup design, automatically switches operators
QoS guarantee mechanism, prioritizes transmission of critical data
Cloud Management Layer:
Data analysis and report generation
Remote device management and firmware updates
Multi-tenant architecture support
2.2 Data Flow Design
Real-time Data Flow:
Batch Data Flow:

AI-Powered Alerts Based on IoT Technology
Chapter 3: Attendance Management Solution for the Cleaning Service Industry
3.1 In-Depth Analysis of Pain Points in Scenarios
The core challenges faced by the cleaning service industry include:
Time Fraud: Employees arriving late, leaving early, or shortening service hours
Location Fraud: Falsely reporting attendance without actually arriving at the service location
Task Fraud: Marking unfinished cleaning tasks as completed
Lack of Evidence: Lack of objective evidence to support claims in case of disputes
3.2 Multi-Factor Validation Mechanism
Spatiotemporal Consistency Validation:
GPS positioning and service location geofence matching
Arrival time and scheduled time window verification
Dwell time and task requirement duration comparison
Biometric Validation:
Face liveness detection to prevent photo fraud
Random face recognition during working hours
Comparison of facial features with employee registration information
Task Completion Validation:
NFC check-in point deployment in key areas
Task step completion sequence verification
Automatic collection of before-and-after cleaning photos
3.3 Anomaly Detection and Early Warning
Behavioral Pattern Analysis:
Establish a baseline for employees' normal work patterns
Real-time detection of behaviors deviating from normal patterns
Multi-dimensional anomaly scoring system
Intelligent Early Warning Mechanism:
Instant anomaly notification to management personnel
Tiered early warning: Reminder, Warning, Critical Warning
Predictive analysis: Identifying potential risk patterns
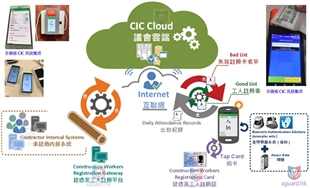
Chapter 4: Logistics and Transportation Industry Transfer Supervision Solution
4.1 Challenges in Transportation and Transfer Scenarios
Special characteristics of the logistics and transportation industry's transfer process:
Geographical dispersion: Multiple transfer stations are widely distributed
Time uncertainty: Arrival time is affected by traffic conditions
Personnel mobility: Drivers and transfer station personnel work together
Cargo diversity: Different goods have different handling requirements
4.2 Person-Cargo Association Verification System
Dual Authentication Mechanism:
Driver authentication: NFC work card + facial recognition
Transfer station personnel verification: NFC work card + facial recognition
Verification of Timestamp Correlation Check
Cargo Association Verification:
Electronic cargo manifest
Photographic evidence of cargo status
Electronic signature for cargo handover
Time and Geographic Association Verification:
GPS location verification upon arrival at transfer station
Comparison of arrival time with scheduled time
Analysis of the match between dwell time and transfer operation duration
4.3 Anti-Collusion Design Principles
Independent Verification Channel:
Separation of driver verification and transfer station personnel verification
Independent upload of verification data, background association comparison
Random cross-verification mechanism
Behavioral Pattern Anti-Tampering:
Unalterable device operation logs
Multi-node time synchronization verification
Abnormal pattern association analysis
Chapter 5: Advantages of Air724 LTE Edge Computing Gateway Technology
5.1 Mobile Communication Performance
High-Speed Transmission Capability:
LTE CAT4, downlink speed up to 150Mbps, uplink speed up to 50Mbps
Supports carrier aggregation technology to improve spectrum utilization
Smart antenna selection to optimize signal quality
Network stability assurance:**
Supports full network compatibility, automatically selecting the best operator
Real-time signal strength monitoring and switching
Automatic reconnection mechanism for network disconnections
Security design:**
Hardware encryption engine, supporting algorithms such as AES, RSA, and SHA
Secure boot and secure firmware updates
End-to-end encryption of communication data
5.2 Edge computing capabilities**
Local computing resources:**
High-performance processor to meet complex computing needs
Large-capacity memory, supporting multi-task parallelism
Local storage buffer to cope with network interruptions
Edge intelligent algorithms:**
Lightweight AI model inference
Data preprocessing and filtering
Rule engine and decision making
Chapter Six: System Stability and Reliability Design**
6.1 Hardware reliability measures
Environmental adaptability design:**
Industrial-grade component selection, wide operating temperature range
Dustproof and waterproof design (IP65 rating)
Electromagnetic interference resistant design, EMC tested
Power supply stability guarantee:
Wide voltage input design (9-36V DC)
Multi-level power protection: overvoltage, overcurrent, reverse connection protection
Backup power design, supports data retention during power outages
6.2 Software stability measures
Fault tolerance mechanism design:
Critical process monitoring and automatic restart
Data transmission retry and breakpoint resumption
Local caching and data recovery mechanism
System monitoring and maintenance:
Remote status monitoring and alarms
Automatic log collection and analysis
Remote diagnostics and troubleshooting
6.3 Network reliability strategy
Multiple connection backups:
Dual network design with LTE as primary and Wi-Fi as backup
Dynamic network quality assessment and switching
Data transmission priority scheduling
Offline operation capability:
Local data storage during network interruption
Offline rule enforcement capability
Automatic synchronization after network recovery
Chapter 7: Compliance and Privacy Protection Design
7.1 Data Privacy Protection
Minimum Necessity Principle:
Only collect data necessary for business operations
Anonymize sensitive data
Data storage time limits
Encryption and Access Control:
Dual encryption at the transport and storage layers
Role-based access control (RBAC)
Complete recording and auditing of operation logs
7.2 Labor Law Compliance
Work Hour Management:
Comply with local work hour regulations
Mandatory implementation of rest periods
Automatic recording and alerting of overtime
Employee Rights Protection:
Protection of personal privacy data
Appeals and dispute resolution mechanisms
Data transparency and right to know
7.3 Industry Standard Compliance
Technical Standard Compliance:
Wireless communication standard compliance
Data format standardization
Interface openness and compatibility
Certification and Testing:
Obtain relevant industry certifications
Third-party security testing
Continuous compliance assessment
Chapter 8: Implementation, Deployment, and Management
8.1 Deployment Strategy
Phase-based Deployment:
Phase 1: Pilot Deployment at Key Sites
Phase 2: Expanding Deployment Scope
Phase 3: Full-scale Promotion and Optimization
Equipment Installation Guidance:
Installation Location Selection and Environmental Assessment
Power and Network Cabling Standards
Equipment Configuration and Initialization Process
8.2 Training and Support
Management Personnel Training:
System Operation and Management Training
Data Analysis and Report Interpretation
Anomaly Handling Process Training
User Training:
Equipment Usage Guidelines
Common Problem Handling
Introduction to Feedback Mechanism
8.3 Maintenance and Optimization
Regular Maintenance Plan:
Equipment Status Check and Cleaning
Software Updates and Security Patches
Performance Evaluation and Optimization
Continuous Improvement Mechanism:
User Feedback Collection and Analysis
Continuous System Function Iteration
New Technology Integration and Upgrading
Chapter 9: Benefit Analysis and Return on Investment
9.1 Direct Economic Benefits
Cost Savings:
Reduced manual verification costs
Reduced direct losses from fraud
Optimized human resource allocation
Efficiency Improvement:
Automated data collection and processing
Real-time monitoring and rapid response
Improved data quality for decision support
9.2 Indirect Benefits
Risk Control:
Reduced compliance risks
Reduced legal disputes
Optimized insurance costs
Brand Value:
Improved service quality
Enhanced customer trust
Increased market competitiveness
9.3 Return on Investment Analysis
Investment Costs:
Hardware costs
Software development and deployment costs
Training and maintenance costs
Payback Period:
Typical case study payback period analysis
Long-term operating cost savings
Potential value of risk avoidance
Chapter 10: Future Development and Technology Outlook
10.1 Technological Development Trends
Enhanced AI Capabilities:
More accurate facial recognition algorithms
Deep learning analysis of behavioral patterns
Predictive maintenance and management
Communication Technology Upgrades:
5G RedCap technology integration
Satellite communication backup
Low-power wide-area network (LPWAN) technology applications
10.2 Application Scenarios Expansion
Cross-Industry Applications:
Construction site personnel management
Field service quality monitoring
Public facility maintenance and management
Functional Expansion:
Environmental quality monitoring
Equipment status monitoring- Energy Management Optimization
10.3 Ecosystem Construction
Platform Openness:
Open and Standardized API Interfaces
Third-Party Application Integration
Ecosystem Partner Development
Community and Support:
Developer Community Building
Technical Documentation and Training Resources
Continuous Technical Support Services
Conclusion
The intelligent attendance and compliance monitoring system based on the ESP32-S3-DEV-KIT-N16R8-M and Air724 LTE edge computing gateway represents a mature application of IoT technology in the field of operations management. The system fully utilizes the low power consumption and high performance characteristics of the ESP32-S3, combined with the wide coverage of LTE mobile communication, to build a stable, reliable, and intelligent monitoring solution.
For the cleaning service industry, the system effectively solves management problems such as false reporting of tasks and late arrivals; for the logistics and transportation industry, the system breaks down information barriers in the transfer process, preventing collusion and fraud. More importantly, while improving management efficiency, the system fully considers compliance and privacy protection requirements, achieving a balance between corporate interests and employee rights.
With the continuous maturation of edge computing technology and the ongoing optimization of artificial intelligence algorithms, such systems will play a vital role in more industries and scenarios, driving the digital transformation of traditional industries and creating greater economic and social value.
--- The technical solutions described in this article are based on publicly available technical materials and general design principles. Specific implementation details need to be customized according to actual business needs. The system design fully considers data security and privacy protection and complies with relevant laws and regulations.
Software Service
Industry information
- Views 8944
- Author :Tony
- Views 603
- Author :Tony
- Views 1661
- Author :Bruce Lee
- Views 41
- Author :Tony
- Views 15
- Author :Bruce Lee
- Views 29
- Author :Tony
































































Hardware & Software Support
We are deeply rooted in Hong Kong’s local services, specializing in hardware and software issues.
System Integration
Hardware and software system integration to enhance stability and reliability.
Technical Support
Professional technical team providing support.
Professional Technical Services
Focused on solving problems with cutting‑edge technologies.